(Plesk for Linux) The Plesk Firewall¶
Caution
Both the Plesk Firewall and firewalld are tools for managing the iptables firewall. Using both tools simultaneously can result in conflicts and in ports required for Plesk to operate being closed. We recommend only using one tool at a time.
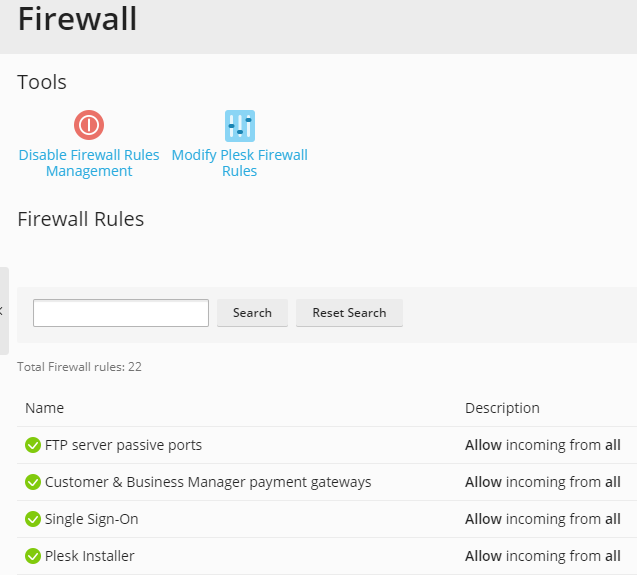
By default, the Plesk firewall configuration consists of policies and rules. Policies are broad in scope and affect all connections to or from the server, depending on the policy itself. For example, you can use System policy for incoming traffic (listed in Tools & Settings > Firewall) to completely block all incoming connections to the server. Rules are narrower in scope and govern incoming connections to individual Plesk services, such as SMTP or MySQL.
Note that rules override policies. For example, if the global policy is to deny all incoming traffic, but a rule allows incoming traffic from a specific IP, the rule takes precedence. You can use this mechanism to easily tighten or relax the security of the server. For example, setting up the policies to forbid all connections to and from the server except for a few allowed IP addresses or ports will result in improved security, but some applications may not be able to work due to the network restrictions. Conversely, allowing all connections by default and using rules to block access to individual services or from individual IP addresses will make your server less secure, but will ensure that you do not run into connection issues. Experiment to find the optimal trade-off between usability and security.
You can manage the firewall in two ways:
- Changing the settings of the default policies and rules.
- Creating custom rules.
To change the settings of the default policies and rules, go to Tools & Settings > Firewall (in the Security group) and click Enable Firewall Rules Management. Confirm enabling rules management, wait for the changes to be applied, then click Modify Plesk Firewall Rules. Click the rule or policy you want to change. You can set a policy to allow or deny connections, and you can set a rule to allow or deny connections, or to allow them from specified addresses only and deny them from all others. Once you have made the changes you wanted, click Apply Changes to make the new ruleset live, or Discard Changes to roll them back.
To add a custom rule, enable firewall rules management as described above and click Add Custom rule. Custom rules are more flexible than the standard ones and can be configured to allow or deny incoming, outgoing, or forwarding connections to or from a specific port or IP address. After you have added one or more custom rules, click Apply Changes to add them to the ruleset, or Discard Changes to discard them. If at a later date you decide to remove one or more custom rules, select the corresponding checkboxes, click Delete, confirm the deletion, then click Apply Changes to remove the selected rules from the ruleset.
When creating custom rules, be careful not to block connections to ports used by Plesk services by mistake.
Note
If you are using Docker containers, Docker firewall rules will not be added to Plesk firewall rules.